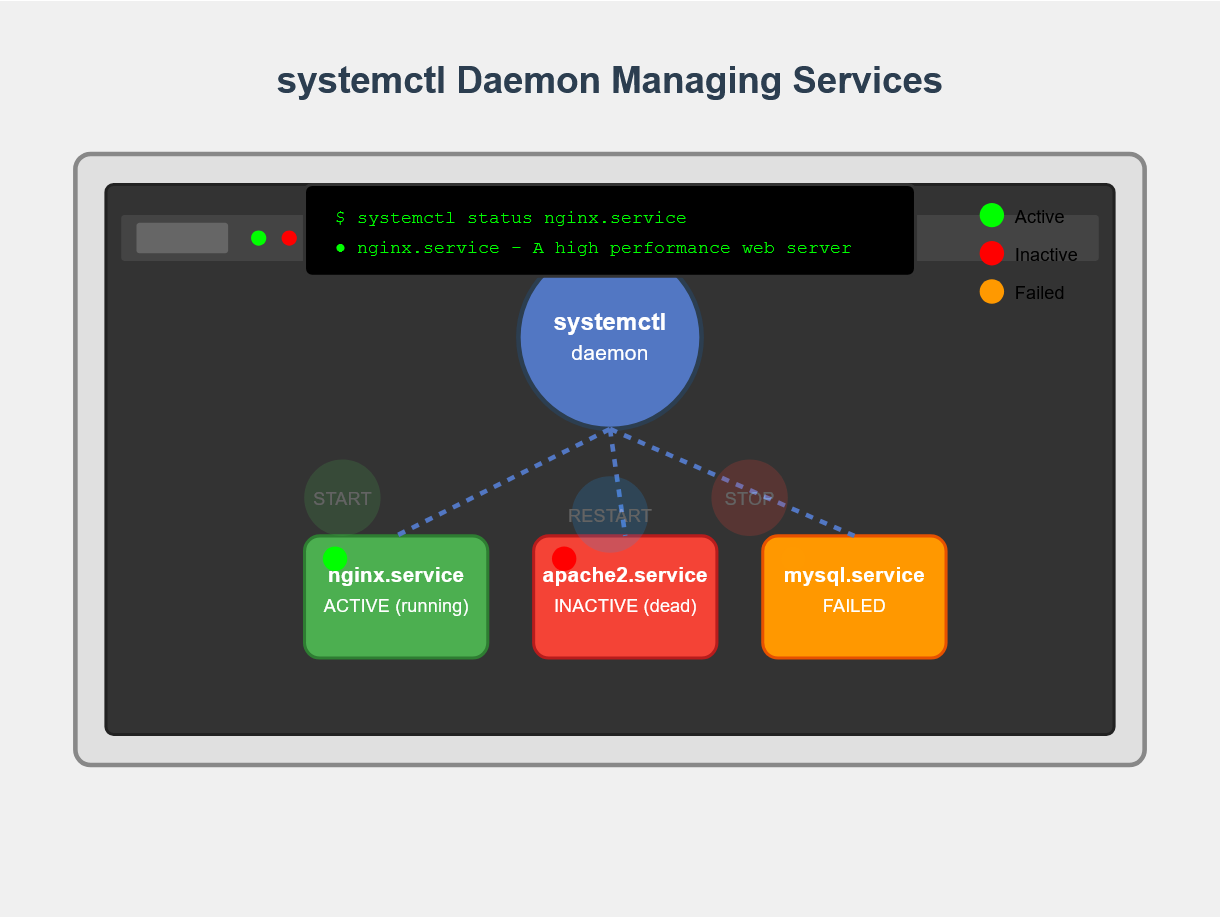
Posted inlinux
Complete Guide to Linux Top Command: Master System Monitoring with Parameters and Examples
The top command is one of the most essential tools for Linux system administrators and users who need to monitor system performance in real-time. This powerful utility displays running processes,…